GDPR FAQ for App developers
Contents
- 1
- 2 Overview of the Regulation
- 3 The GDPR main actors
- 4 The top 8 frequent questions
- 4.1 1. What does GDPR mean for App developers, dev shops, platform providers and how can they prepare?
- 4.2 2. When does GDPR come into force?
- 4.3 3. What are the GDPR fines and penalties for non-compliance?
- 4.4 4. Am I a Data Controller or a Data processor?
- 4.5 5. What am I supposed to do with user data to comply with GDPR?
- 4.6 6. What is User trust?
- 4.7 7. In case of data loss, how should I proceed?
- 4.8 8. What does GDPR compliance look like?
- 4.9 What is privacy by design concept of GDRP?
- 4.10 What are essential actors of GDRP?
- 4.11 Who is responsible for data of application users?
On May 25, 2018, the European General Data Protection Regulation (GDPR) that has been in the pipeline for a couple of years now goes into effect across European Union EU and European Economic Areas EEA. This has replaced the old privacy laws of 1995. It is a much tougher regime now, not least because companies must adhere to a new framework that creates consistent and reliable data protection rules across the EU and EEA. All businesses that process the personal data of individuals in the EU and EEA must comply with the GDPR or risk strict penalties and fines. The regulators will be able to impose hefty fines on organizations that misuse customers/citizens personal information.
The GDPR introduces new concepts such as privacy by design, the requirement to be able to demonstrate compliance (i.e. Comply and be seen to comply) and places a much stronger emphasis on making sure people are kept informed and have a say on what is done with their personal information. It also keeps a spotlight on the security and location of the data; which are seen as particular areas of risk. If you are new to the GDPR, this article-series which has been updated in light of the final text formally adopted by the European Parliament and the Council of Ministers, which include clarifications on data portability, data protection officers, and lead supervisory authorities will be of enormous help.
Overview of the Regulation
The goal to enact the EU GDPR began in 2012, and this was a major update to the previous EU Data Protection Directive that was first published in 1995. Its main purpose was to harmonize the laws across the 28 member states; clear up areas that were previously interpreted differently in different member states; increase its scope to include any organization or individual that collects data on EU citizens, and ensure that the regulations are enforced in a similar manner across all states.
Any organization that collects(Data controller), stores and/or processes(Data processor) data on living individuals of the EU and EEA must conform to this regulation and incorporate appropriate policies and technology to toe the line.
GDPR top 10 highlights
Though the full regulation covers many areas, let us take a quick overview of the top ten provisions getting the most attention.
1- The new and increase penalty/fines can be up to 4% of global turnover or €20M, whichever is higher would be implemented;
2- Users must give clear consent for data controllers and processors to collect & use their data and controllers & processors must only use it for the purpose defined. (I.e. Opt-in consent);
3- The local supervisory authority must be informed within 72 hours of any data loss and users informed immediately (i.e. Breach notification);
4- Any organization with data on EU individuals must conform, wherever they are based. (I.e. Territorial scope);
5- Data controllers and data processors are both liable for data loss incidents. (I.e. Joint liability);
6- Users must have total control over its data. They have the right to demand the removal/portability/deletion of their data.;
7- One law across the EU/EEA (i.e. what is obtainable in one member state is applicable to all other member states);
8- Transferring data outside the EU is allowed, but the data controller is always ultimately responsible if data is lost via a non-EU cloud provider;
9- The enforcement agencies are expected to enforce consistency across all the countries. (I.e Common enforcement);
10- Users can work together to sue using class action lawsuits.(I.e Collective redress);
The above top ten provisions are the major focuses in the GDPR, now that you know the meaning of GDPR, let us look into details the most pertinent questions that arise from this overview. Below are the frequently asked questions and answers which provide a handy reference that explain if you are affected by the current law and what you need to know about GDPR because Data protection is of utmost importance to the Back4App customers.
Do you need a GDPR enalbed backend? Join now to Back4App.
The GDPR main actors
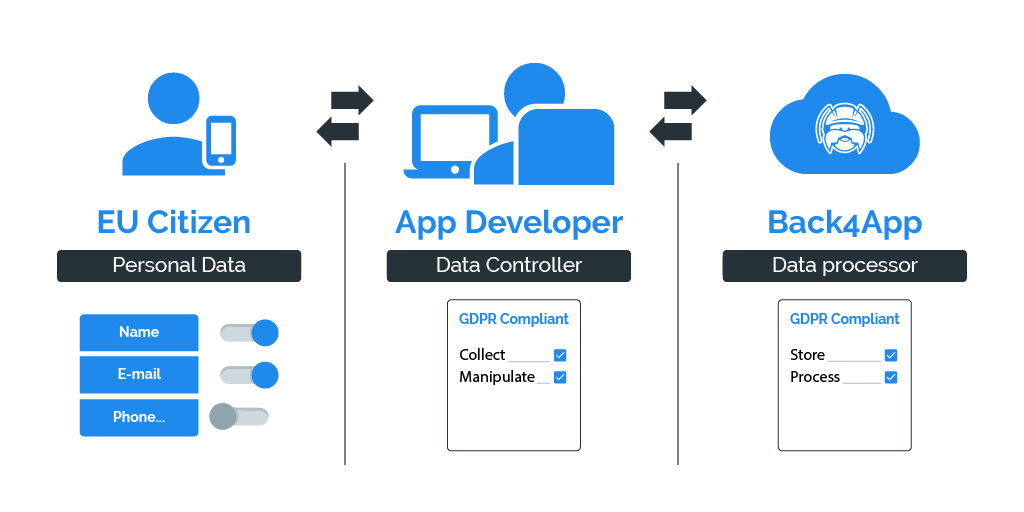
1. User’s(Data Subject) personal data
The types of data considered personal under the 1995 EU Data Protection Directive published (Directive 95/46/EC) to regulate the collection, processing and free movement of data on individuals within the European Union include name, address, and photos. GDPR extends the definition of personal data to mean any information related to an identifiable natural person like(but not limited to) physical, physiological, social, mental, genetic, economic.
Some practical examples are the name, email, date of birth, phone number, ID number, location data, health data. All the online information of all devices related to the user is also included in this list like IPs, MAC Addresses, cookies, RFID tags, or any other online information related to the user. Also, it’s indicated to consider any information that can be combined to identify a person as a personal data. Such sensitive personal data are some of what makes the GDPR different from old regulation. At this point, the law is written in a very broad way to stand the test of time.
2. Data Controller
As laid down by the GDPR law a controller is “person, public authority, agency or other bodies which, alone or jointly with others, determines the purposes and means of processing of personal data”, Control, rather than possession, of personal data is the determining factor here. The data controller is the person (or business) who determines the purposes for which, and the way in which, personal data is processed. Being a data controller carries with it most of the GDPR legal responsibilities, so you should be quite clear if these responsibilities apply to you.
App developers are in most cases the data controllers, but depending on the case they can be both data processors and data controllers. If an app developer/provider is using a self-hosting structure, for example, he is both data controller and data processor. If you are in any doubt or are unsure about the identity of the data controller in any particular case, you should consult your legal adviser or seek the advice of the Data Protection Commissioner. Data controllers can be either individuals or “legal persons” such as companies, Government Departments, and voluntary organizations.
3. Data Processor
The processor is “person, public authority, agency or other bodies which processes personal data on behalf of the controller. This could refer to a third party. , if you hold or process personal data, but do not exercise responsibility for or control over the personal data, then you are a “data processor”. Examples of data processors include hosting companies, BaaS (like Back4App), payroll companies, accountants, and market research companies, all of which could hold or process personal information on behalf of someone else. “Cloud” providers are also generally Data Processors.
It is possible for one company or person to be both a data controller and a data processor, in respect of distinct sets of personal data. For example, a payroll company would be the data controller in respect of the data about its own staff but would be the data processor in respect of the staff payroll data it is processing for its client companies. A data processor is distinct from the data controller for whom they are processing the personal data. An employee of a data controller, or a section or unit within a company which is processing personal data for the company as a whole, is not a “data processor”. However, someone who is not employed by the data controller, but is contracted to provide a particular data processing service (such as a tax adviser, or a telemarketing company used to manage customer accounts) would be a data processor. A subsidiary company owned by a data controller to process personal data on its behalf (for example to manage the payroll) is a distinct legal person and is a data processor.
The definitions of data-handlers by the legislation in article 4 of the GDPR stated categorically those data processors and data controllers are jointly liable for any breach of information. These obligations for processors are a new requirement under the GDPR. Also, Controllers will also be forced to ensure that all contracts with processors are in compliance with GDPR.
GDPR eventually places legal obligations on a processor to maintain records of personal data and how it is processed, providing a much higher level of legal liability should the organization be breached.
The top 8 frequent questions
1. What does GDPR mean for App developers, dev shops, platform providers and how can they prepare?
GDPR describes “personal data” as the recording of any data that could identify a natural person, the term Identifiers, in this case, can include names, phone numbers, and addresses, as well as digital information, such as emails, usernames, locations, age, sex, buying behavior and more. This regulation, therefore, affects mobile app developers as well.
App developers and service providers are totally responsible for their users’ data. App developers must make sure they have complete visibility and control over app usage and activity. They must first learn and understood everything about how they obtain, store, transfer and use data, to improve security. Upgrades to servers and new firewall configurations are very important at this stage.
Developers and service providers must also keep track of changes within the data, as well as digital and physical access to it, which invariably means that a complete history of changes must be documented. Any data that travels between the app and the server should be encrypted and secured. And also Know your technology and potential weak links that could be exploited by hackers.
Below is how App developers can reduce the risk with the Service providers they work with, to avoid GDPR violations and minimize their exposure:
- Study the service provider to understand what data is stored and processed, how well it protects personal data, and how they are working towards becoming GDPR compliant.
- Study your own data locations ensure the data is protected.
- Make sure you have a strong internal security policy in place.
- Decide whether you need to hire a Data protection officer DPO.
- Inquire and make sure that the Service provider you work with doesn’t gather and save data in their own databases.
- Map out the path the data takes during the processing lifecycle to ensure adequate security is implemented at each stage.
- Make sure that the service provider has adequate security measures to ensure the safety of your users’ data. Include strict confidentiality, data privacy and data residency clauses in any contract drawn up.
Do you need a GDPR enalbed backend? Join now to Back4App.
2. When does GDPR come into force?
As I said earlier GDPR has come into full force across the European Union on 25 May 2018, and all member nations are expected to have already transferred it into their own national law by 6 May 2018.
After four years of intense preparation and debate, GDPR was finally approved by the European Parliament in April 2016 and the official texts and regulation of the directive were published in all of the official languages of the EU on May 2016.
3. What are the GDPR fines and penalties for non-compliance?
Failure to comply with GDPR can result in a penalty ranging up to 20 million euros or four percent of the company’s annual global turnover, whichever is higher will be used.
Penalties will depend on the severity of the breach and on whether the company is deemed to have taken compliance and regulations around security in a serious enough manner.
The maximum fine of 20 million euros or four percent of worldwide turnover — whichever is higher is for infringements of the rights of the data subjects, unauthorized international transfer of personal data, and failure to put procedures in place for or ignoring subject access requests for their data.
A lower fine of 10 million euros or two percent of worldwide turnover will be applied to companies which mishandle data in other ways. They include, but not limited to; failure to report a data breach, failure to build in privacy by design and ensure data protection is applied in the first stage of a project and be compliant by appointing a data protection officer — should the organization be one of those required to by GDPR.
4. Am I a Data Controller or a Data processor?
Even when a detailed explanation above is given, sometimes it’s still difficult to differentiate between a data controller and a data processor,to answer this question you should ask yourself the following question:
- Does my company collect and manipulates information of living EU citizens?
- Does my company processes and/or stores information of living EU citizens?
If the answer is YES to the first question you are a data controller.
If the answer is YES to the second question you are a data processor.
If the answer is YES to both you are both data controller and processor.
5. What am I supposed to do with user data to comply with GDPR?
In GDPR the user is in charge. The basic requirement to a data controller comply with GDPR is to give (and let him know that explicitly) the user the total control under his data. That means to allow user access all his data, to request deletion of all the data, to request corrections, to know the source of all his data, how long its data will be kept in the data controller.
At any moment the user may request a portability of its data to keep with him or to transfer to another data controller. In case of any issue, the user may communicate to the supervisory authority that the data controller is not complying with the GDPR.
5.1. What is User Right of Acess?
Data subjects under the GDPR have the right to contact any data controller and ask for the information that has been collected and the data controller has to respond within a stipulated time. This gives the data subject the privilege to confirm that the data is correct and allows the data subject to transfer the same data to another data controller if the need arises.
5.2 What is User right of correction and deletion?
The regulation states that data should only be kept for the period it is needed and should be deleted immediately after that period elapse. Data subjects have the right to demand for data held on them to be corrected or deleted by the data controller, The data controller must obey and respect the decision of the data subject or else the hefty fine stated on the GDPR will be placed on them by the regulatory authority. There must be evidence that the data has been corrected or deleted by the data controller. Data controllers need to have a process in place that allows them to correct and delete data easily with an evidence to show the regulatory authority or the data subject.
5.3 Can I use user data for marketing?
Data subjects can object not only to the collection of their data for direct marketing but also to the profiling of them by direct marketing agencies. As direct marketing agencies use ever more sophisticated profiling to improve their targeting, this is called out specifically in the regulation.
One important point is that the right to object should be brought to the attention of the data subject separately from other information, ensuring that the data subject can choose whether some or all of their data is used for direct marketing separately from its use for other reasons.Those in the retail and marketing sectors will now need to request for customer consent to have their email in their database with the option to opt-out at any time they wish to do that.
5.4 What is ‘right to be forgotten’?
Is a process, which provides additional rights and freedoms to customers who no longer want their personal data processed to have it deleted, providing there are no grounds for retaining it. Organizations must keep these consumer rights in mind now that the GDPR have come into effect.
5.5 What kind of data should I make accessible to final user?
The kind of data that you should make accessible to the final user is data that has been pseudonymized. ‘pseudonymization’ of data means the identifier is replaced by a different, unique identifier that can be derived from the original data, e.g., through a cryptographic hash function. The link between these two identifiers can be stored in an Identity Store. This makes the data more accessible and subject to less stringent security requirements,
5.6 How to comply with user deletion?
If a data subject demand for data deletion the data controller should oblige and delete the data as requested by the data subject and show the regulatory authority or data subject an evidence that the data has been deleted.
6. What is User trust?
The regulation includes a paragraph encouraging certification bodies and mechanisms to be defined that data controllers could join to show their commitment to data protection standards. It is probably likely that these will appear shortly. Hopefully, these bodies will have strong data privacy safeguards that will give data subjects more confidence to share their data with those organizations that join.
7. In case of data loss, how should I proceed?
In the event of a company losing data, be it as a result of a cyber attack, human error or anything else, the company will be obliged to deliver a breach notification. This must include approximate data about the breach, including the categories of information and number of individuals compromised as a result of the incident and the categories and approximate numbers of personal data records concerned. The latter takes into account how there can be multiple sets of data relating to just a single individual.
Organizations will also need to provide a description of the potential consequences of the data breach, such as theft of money, or identity fraud, and a description of the measures which are being taken to deal with the data breach and to counter any negative impacts which might be faced by individuals. The contact details of the data protection officer, or main point of contact dealing with the breach, will also need to be provided.
8. What does GDPR compliance look like?
GDPR might seem complex, but the truth of the matter is that the top 10 overview listed at the beginning of this guide contains the most part of the legislation. However, there are elements of GDPR such as breach notification and ensuring that someone is responsible for data protection which organizations need to address or run the risk of a fine.
There’s no ‘one size fits all’ approach to preparing for GDPR. Rather, each business will need to examine what exactly needs to be achieved to comply and who is the data controller who has taken responsibility for ensuring it happens.
“You are expected to put into place comprehensive but proportionate governance measures to minimize the risk of breaches and uphold the protection of personal data. Practically, this is likely to mean more policies and procedures for organizations, although many organizations will already have good governance measures in place.”
That could be the responsibility of an individual in a small business, or even a whole department in a multinational corporation. Either way, budget, systems, and personnel will all need to be considered to make it work.
Under the GDPR provisions that promote accountability and governance, companies need to implement appropriate technical and organizational measures. These could include data protection provisions (staff training, internal audits of processing activities, and reviews of HR policies), as well as keeping documentation on processing activities. Other tactics that organizations can look at include data minimization and pseudonymization or allowing individuals to monitor processing.
The full regulation is available to view here.
Do you need a GDPR enalbed backend? Join now to Back4App.
What is privacy by design concept of GDRP?
GDRP has introduced a recent concept named privacy by design. This is the requirement which can make you able to demonstrate compliance. Even more, it places a stronger emphasis on ensuring that people are kept informed regarding what is going to be done with their personal details. This concept will also highlight location and security of data.
What are essential actors of GDRP?
Here are the major GDRP actors you need to know:
-Personal data of app users
-Data processor
-Data controller
Who is responsible for data of application users?
Application developers as well as service providers are responsible for the data of their application’s users. Applications developers need to ensure they have thorough control and visibility over their application’s activity and usage. While, service providers and developers must keep changes’ track within data and its physical and digital access.